Developers Access to Aws Which Managed Policy to Use
Im trying to keep duplication to a minimum and it seems like I may be able to achieve it via a Policy linked to a role and group of users. MM_APPS_AWS_ACCESS_KEY An AWS Access Key ID for mattermost-apps-invoke user.

Deploying Defense In Depth Using Aws Managed Rules For Aws Waf Part 2 Aws Security Blog
This method is available on instances of the Role User and Group classes.

. Services do not remove permissions from an AWS managed policy so policy updates wont break your existing permissions. This lets you avoid having to store and manage AWS credentials in Azure. New in version 100.
For example the ReadOnlyAccess AWS managed policy provides read-only access to all AWS services and resources. To use it in a playbook specify. This policy grants permissions to create configure and maintain databases.
Its 11 trust relationship. This policy grants full access to all AWS services except for IAM. From left navigation pane click on Policies.
MM_APPS_AWS_REGION The AWS region to use. None of these policy templates grants permissions for any SSM operation so you cant use a SAM policy template to grant your AWS Lambda function access to SSM parameters as of now. Access to the following AWS services is included in this policy.
The following trust policy lets Lambda service assume this role. This secret-less model can be used even when these services need to access Amazon Web Services AWS resources. Each instance in an auto scale configuration is assigned an IAM Instance Role that has a policy.
For more information see IAM and STS quotas. Administrator step 2. The fastest and easiest way was to use an IAM user access key and secret to access.
Example use case to attach policies to a developer group. If appsctl aws init --create-access-key was used it can be found once in the commands output. In order to attach a managed policy to an IAM entity after the entity has been created we have to use the addManagedPolicy method.
Lets say youre using a group in IAM named AirflowDevelopmentGroup to apply permissions to all of the developers on your Apache Airflow development team. Using the tool credentials can be obtained programmatically for your existing Stax identity in AWS accounts. This removes the requirement to generate long-lived IAM Users and associated secrets.
It specifies the privileges for your limited IAM. This policy grants permissions required for setting up and configuring network resources. Amazon Route 53 Route 53 Domains Amazon VPC and AWS Direct Connect.
This post explains why these policies are simultaneously very appealing and dangerous to use. SSH keys View Answer Answer. Click on the Visual editor tab then at the right select the option Import managed policy.
MM_APPS_AWS_SECRET_KEY The Secret Key for the access key above. Even though they have long been considered a security weakness they are still very popular. It includes access to AWS database services such as Amazon DynamoDB Amazon Relational Database Service RDS and Amazon Redshift.
The size of each managed policy cant exceed 6144 characters. To determine whether a permission is specific to a KMS key see AWS KMS permissions and look for a value of KMS. AWS Managed Policies are a widely-used feature of AWS Identity and Access Management IAM which enables out-of-the-box access to AWS resources.
Identity-based policies managedinline can be attached to a role afterwards by using attach-role-policy or put-role-policy commands. Based on your scenario complete the steps in one of the following. The same policy is applied to the user when they try and access these instances.
Create a policy with limited IAM administrator permissions by using the AWS CLI. AWS Identity and Access Management IAM now enables Amazon Web Services AWS administrators to use tags to manage and secure access to more types of IAM resources such as customer managed IAM policies Security Assertion Markup Language SAML providers and virtual multi-factor authentication MFA devices. You have to provide this file as input to the command using assume-role-policy-document option.
Inline policy is policy that you attach directly to an identity. View the policy for the full list of database services that this policy supports. Attaching Managed Policies on IAM Entities in AWS CDK.
AWS managed policy is policy that AWS already provided and customer managed policy is the custom policy created by customer itself based on what they need and create it as the new policy with the new name. This ability is powerful and might be used inappropriately or accidentally to attach an administrator access policy to obtain full access to all resources in an account. When you delete the user the inline policy.
Which AWS IAM feature allows developers to access AWS services through the AWS CLIA. The code for this article is available on GitHub. Delegate permission management to developers by using IAM permissions boundaries.
Fortunately there is a better way to securely access AWS services without exposing client secrets see diagram below. Ansible-galaxy collection install communityaws. MM_APPS_S3_BUCKET The name of the.
D Latest CLF-C01 Dumps Valid Version with 721 QAs Latest And Valid QA Instant Download Once Fail Full Refund Instant Download CLF-C01 PDF. These users need access to the AmazonMWAAFullConsoleAccess AmazonMWAAAirflowCliAccess and AmazonMWAAWebServerAccess permission policies. When a service launches a new feature AWS.
You can attach a maximum of 10 managed policies to an IAM role or user. Your IAM managed policy can be an AWS managed policy or a customer managed policy. You can also use an AWS managed policy as a permissions boundary.
Additionally AWS supports managed policies for job functions that span multiple services. When these services are running in Azure developers can use managed identities in Azure to avoid dealing with credentials on their own. Stax2aws is a Command Line Interface CLI tool to gain AWS credentials for Stax-managed AWS accounts.
First you will create the MyProjectLimitedAdminAccess policy. What you can do as a workaround is to manually add the required policy statement inline to your policies. A user will need to authenticate first with Cognito to get his own access tokens that have an expiry.
You will then create the MyProjectS3Access policy and attach it to the project developer myprojectdev1 along with the AWS managed policy AmazonDynamoDBFullAccess. To install it use. To check whether it is installed run ansible-galaxy collection list.
Permissions in this policy that are specific to a KMS key such as kmsTagResource and kmsGetKeyRotationStatus are effective only when the key policy for that KMS key explicitly allows the AWS account to use IAM policies to control access to the key. A tag is an attribute that consists of a. To do this a developer needs to expose these access keys.

Aws Account Structure Think Twice Before Using Aws Organizations Cloudonaut

Preparing On Premises And Aws Environments For External Kerberos Authentication For Amazon Rds Aws Database Blog
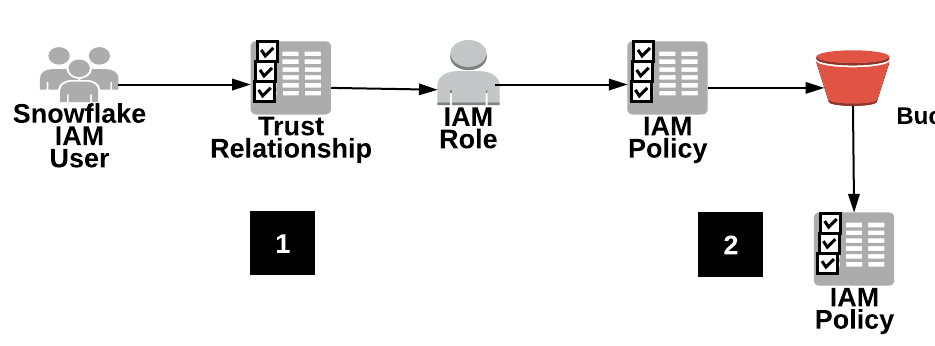
Option 2 Configuring An Aws Iam Role To Access Amazon S3 Deprecated Snowflake Documentation
No comments for "Developers Access to Aws Which Managed Policy to Use"
Post a Comment